Considering the fact that the speed of digital data exchange has been constantly increasing in recent years, ensuring information security when receiving, storing and transmitting data comes to the fore.
In order to minimize the risk of information falling into the wrong hands, it is necessary to use an encryption procedure so that only the intended recipient can access the data. One of the simplest types of coding is the Caesar cipher.
Given the widespread use of Internet technologies, information security problems are emerging more and more often, and the protection of confidential information is of the greatest importance in Internet banking. In the vast majority of cases, the provider is obliged to ensure the security of its own infrastructure, as well as the protection of personal data and applications of customers, while the latter must make sure that the provider has taken all necessary measures to ensure information security.
In order to minimize the risks of personal data falling into the wrong hands, the data must be converted into an unreadable form, and this procedure is carried out on the sender’s side, after which, already on the recipient’s side, the reverse transformation into a readable form takes place. Thus, it can be argued that the problem of maintaining confidential information is of particular relevance for both individuals and large companies.
Cryptography
The science of protecting information from falling into the wrong hands, by converting it into a form that attackers are unable to recognize both during storage and issuance, has existed for more than two thousand years.
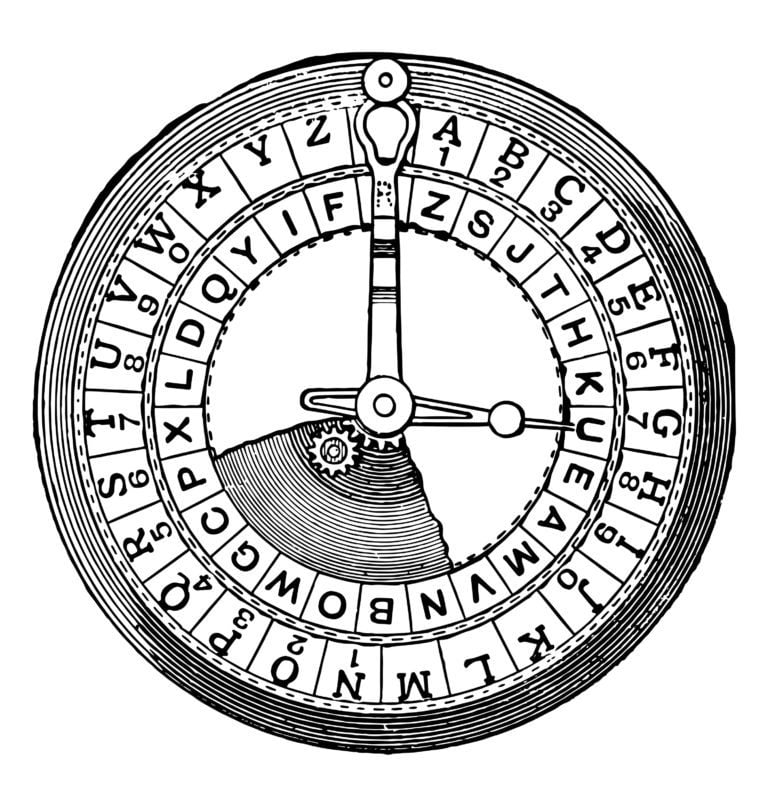
The very concept of cryptology comes from two words meaning “hidden” and “write”, which makes communication incomprehensible to all but the intended recipients. A message that is supposed to be sent is called plaintext, while one that is actually sent is already encrypted text. It is customary to distinguish two main types of cryptography, which, depending on the type of security keys used to encrypt and then decrypt data, asymmetric and symmetric encoding methods.
Symmetric Encryption
Symmetric key cryptography involves the use of a single key for both encryption and decryption, a technique known as private key cryptography that can be updated to provide additional keys.
This approach, in comparison with the asymmetric one, is more efficient and efficient, and the key is generated by the appropriate encryption algorithm, which is then sent to the recipient section. The symmetric encryption method is riddled with a number of problems, since there are practically no secure channels in nature, and therefore the key is transmitted along with the data, which significantly reduces bandwidth efficiency, while increasing costs.
Asymmetric encryption
This type of encryption is called public key cryptography, and two keys are used, one of which, used for encryption, is public and known to the general public, while the second, used for decryption, is known only to the user of the corresponding key and is private. By mathematically associating the keys, data encrypted using the public key can only be decrypted by the corresponding private key, thereby solving the problem of symmetric key management encryption. However, this unique nature of public key encryption makes it more vulnerable to attack.
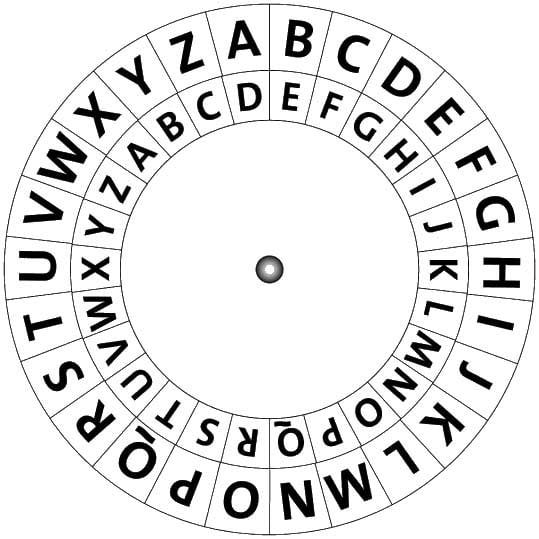
In addition, asymmetric encryption methods, which require significant computing power, are almost a thousand times slower than symmetric encryption. As methods for converting data into an unreadable form, methods related to permutation and replacement are usually used. One example of a substitution method is just the Caesar cipher, which is distinguished by a fairly simple encryption and decryption algorithm. In order to decrypt the system, one does not even need to know the encryption key, which is easy enough to crack by changing the order of the encryption and changing the order of the alphabet.
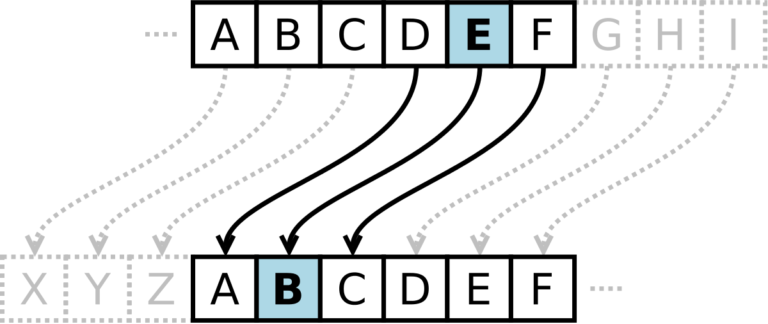
In the event that it is reliably known that the Caesar cipher was used in the encoding, then in order to perform brute-force cryptanalysis, it will only be necessary to sort through 26 keys, in relation to the English language, given the popularity of encryption and decryption. In addition, if one letter has become known, then by determining the offset, you can quickly decrypt the entire message. One of the most common methods used in cryptanalysis is “Frequency analysis”, which assumes that in long texts, and for different texts of the same language, the frequency of occurrence of a given letter of the alphabet does not change. The method of frequency cryptanalysis gained particular fame in 1822, in the process of deciphering Egyptian hieroglyphs. Since the middle of the last century, the development of the vast majority of encryption algorithms has been carried out taking into account the resistance to frequency cryptanalysis, and therefore it is usually used in the process of training future cryptographers.
How to decipher the Caesar cipher
The first situation allows cracking using the methods used for a simple substitution cipher, since using similar solutions, such as frequency analysis, it will be possible to quickly notice the regularity used in the solution, based on which we can conclude that the coding system used is a Caesar cipher . The second situation is even more simple, since for example, English, there are only 25 shift options that can be tested using the brute force method. Thus, it is possible to write out a piece of text that has been encoded in a column of all possible shifts, using a technique known as “completing a simple component.”
In the event that there is a plain text written in natural language, then the decoding option is likely to be the only one, while when using sufficiently short messages, a number of decryption options are possible, taking into account various shifts. The most interesting thing is that the procedure, which involves multiple encryption, does not increase the degree of resistance to hacking.
Output
The Caesar cipher is one of the simplest types of encryption, often combined with other techniques. Currently, encryption, both by substitution and permutation, is carried out using computers, and in order to obtain a sufficiently safe and reliable cipher, a combination of classical methods should be used.